CTF writeup : Gemastik XVI Cryptography Challenges
04 Aug 2023
Tiga soal kategori cryptography tersebut adalah :
easy AES
Soal
Description
Attack on AES OFB
File
Solution
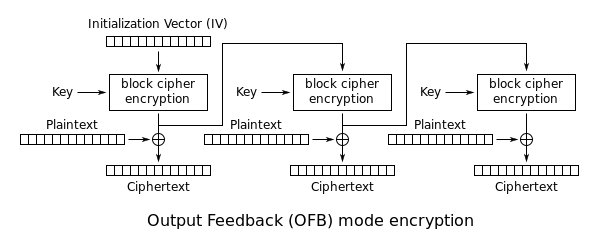
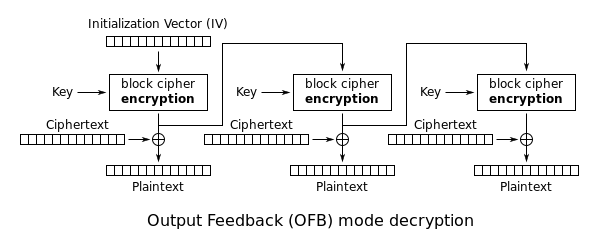
Berikut ini adalah full solvernya.
#!/usr/bin/env python3
from patsac import *
if not args.LOCAL:
with open("nc.sh") as f:
NC = f.read().strip().split()
f.close()
SRVR = NC[1]
PORT = NC[2]
r = remote(SRVR, PORT, level="warning")
else:
r = process("./chall.py", level="debug")
def main():
r.sendlineafter(b"> ", b"2")
r.recvuntil(b"ciphertext = ")
ct0 = int(r.recvline(0).decode())
r.sendlineafter(b"> ", b"1")
r.sendlineafter(b"plaintext = ", str(ct0).encode())
r.recvuntil(b"ciphertext = ")
ct1 = int(r.recvline(0).decode())
secret = str(bytes_to_long(long_to_bytes(ct1)[:128])).encode()
r.sendlineafter(b"> ", b"3")
r.sendlineafter(b"secret: ", secret)
print(r.recv().decode())
return 0
if __name__ == "__main__":
main()
Flag
gemastik{33d4cfb92569d8f21851f9c3dc96c244c3e344064ffb0b35603a550802b7531e}
Note: Flag dinamis, berubah setiap interval tertentu.
References
k-1
Soal
Description
Shamir said we need k shares to recover the secret.
File
Solution
Berikut adalah full solvernya.
#!/usr/bin/env python3
from patsac import *
if not args.LOCAL:
with open("nc.sh") as f:
NC = f.read().strip().split()
f.close()
SRVR = NC[1]
PORT = NC[2]
r = remote(SRVR, PORT, level="warning")
else:
r = process("./chall.py", level="debug")
def main():
k = r.recvline(0)
xy = r.recvline(0)[1:-1].split(b", ")
x, y = int(xy[0]), int(xy[1])
ans = str(y % x).encode()
r.sendlineafter(b"password: ", ans)
print(r.recv().decode())
return 0
if __name__ == "__main__":
main()
Flag
gemastik{a5061d673d03123fe19bbbcc853da16c9f6fee9e55c26f2c9b7b937b60c0ec83}
Note: Flag dinamis, berubah setiap interval tertentu.
naughty-boy
Soal
Description
La La La - Naughty Boy Lyrics La La, La La La La La na na na na na La La na na, La La La La La na na na na na La La, La La La La La na na na na na La La na na, La La La La La na na na na na
File
Solution
Berikut ini adalah full solvernya.
#!/usr/bin/env python3
from patsac import *
if not args.LOCAL:
with open("nc.sh") as f:
NC = f.read().strip().split()
f.close()
SRVR = NC[1]
PORT = NC[2]
r = remote(SRVR, PORT, level="warning")
else:
r = process("./chall.py", level="debug")
def recon():
global r, SRVR, PORT
r.close()
if not args.LOCAL:
r = remote(SRVR, PORT, level="warning")
else:
r = process("./chall.py", level="debug")
def prev_prime(n):
n -= 2
n |= 1
while not isPrime(n):
n -= 2
return n
def main():
global r
while True:
e = 65537
r.recvuntil(b"c = ")
c = int(r.recvline(0))
r.recvuntil(b"n = ")
n = int(r.recvline(0))
r.recvuntil(b"modd = ")
modd = int(r.recvline(0))
if modd % 4 != 3:
print("Nilai modd belum cocok. Reconnecting...")
recon()
continue
r.recvuntil(b"hint_1 = ")
hint1 = int(r.recvline(0))
r.recvuntil(b"hint_2 = ")
hint2 = int(r.recvline(0))
# hitung nilai hidden_val dengan 2 kali hitung quadratic residue
test = pow(hint2, divexact(modd + 1, 4), modd)
test = pow(test, divexact(modd + 1, 4), modd)
if test.bit_length() > 1280:
test = -test % modd
# hitung nilai asli hidden_val (kurangin dengan rand_1)
rand1 = test % n
z123 = test - rand1
# prediksi nilai z3
z3 = divexact(z123, n)
while z3.bit_length() >= 256 and rand1.bit_length() <= 1035:
z3 = prev_prime(z3)
z123 = n * z3
rand1 = test - z123
if z3.bit_length() == 256 and rand1.bit_length() == 1035:
# cari nilai z2
sisa = hint1 % pow(z3, 8)
z32 = hint1 - sisa
z2 = int(divexact(z32, pow(z3, 8)))
# kalau n % z2 == 0, artinya inilah z3 yang benar
if n % z2 == 0:
break
# dekripsi rsa seperti biasa
z1 = divexact(n, z2)
phi = (z1 - 1) * (z2 - 1)
d = pow(e, -1, phi)
secret = str(pow(c, d, n)).encode()
r.sendlineafter(b"What is the secret: ", secret)
r.recvuntil(b"GG! Here is your prize:\n")
print(r.recvline(0).decode())
break
return 0
if __name__ == "__main__":
main()
Flag
gemastik{643dba5a7e68ce4f395bc78ed366284baa146d2f7f76cd507128fc8a6dba910d}
Note: Flag dinamis, berubah setiap interval tertentu.
